Ideal Data Memory (IDM) - A technological breakthrough in security and safety of stored and transmitted information

The 21st century is the age of information. More and more data are generated on the daily basis creating an ever increasing demand for storage space. Not every home computer, let alone a mobile device, can store all its own generated data. The capacity of the built-in memory is growing along with requirements for data safety. The increased volume of generated data proportionally increases the number of potential threats to the storage of this data. With the growth in the number of devices, cloud storage services are becoming increasingly important.
Many cloud storage providers promise fast, reliable and convenient services. However, the reality is a bit more complicated.
Pure statistics
o The year 2013 was marked by a scandal involving the outdated SSL service certificate by Microsoft Azure, which provided criminals with an opportunity to hack the Xbox Live system;
o The so called Celebgate incident, which happened in 2015, when hackers stole intimate photos of celebrities from the iCloud (Apple) cloud storage;
o The number of hacks inflicted on cloud services is growing every year at the rate around 50%;
o Approximately 70% of companies have at least one application running in a cloud; Ultra - Secure Digital Data Storage Service 9
o Lloyd's of London and Cyence believe that a massive attack on cloud storage can cause losses in excess of $ 5 billion, and only 15 -17% of the total amount will be covered by insurance;
o In 2017, the data storage of Equifax, the US leading consumer credit report agency, had been hacked resulting a personal data loss of 143 million customers. Consequently, the value of company's stocks has plummeted by 13%;
o The absence of two-factor authentication resulted in a personal data theft of 80 million customers of Anthem, an American health insurance company.
- Data loss in cloud storage
- Theft of data from cloud storage
- Network Attack
- DDoS Attack
- Human Factor
Rough estimates suggest, as a result of a cybercriminals’ activity, the global economy loses $ 114 billion annually. Since the emergence of the World Wide Web, the United Stated alone suffered losses of around $400 billion. This is three times more than the country’s annual budget for education.
NOW HERE COMES THE REVOLUTION
Please watch video below
https://myidm.io/video/idm_720p_en.mp4
IDM
IDM has its own patented data protection technology called SIZE and is preparing to launch a new service - a global decentralized ecosystem that connects users who want to store information safely and miners who provide memory on their devices to generate income. Our development team has created a working prototype of a cloud storage service called BoobookBox. The service was launched in 2015 and has more than 2 thousand active users. The working prototype was launched to test the technology, both by developers and third- party organizations.
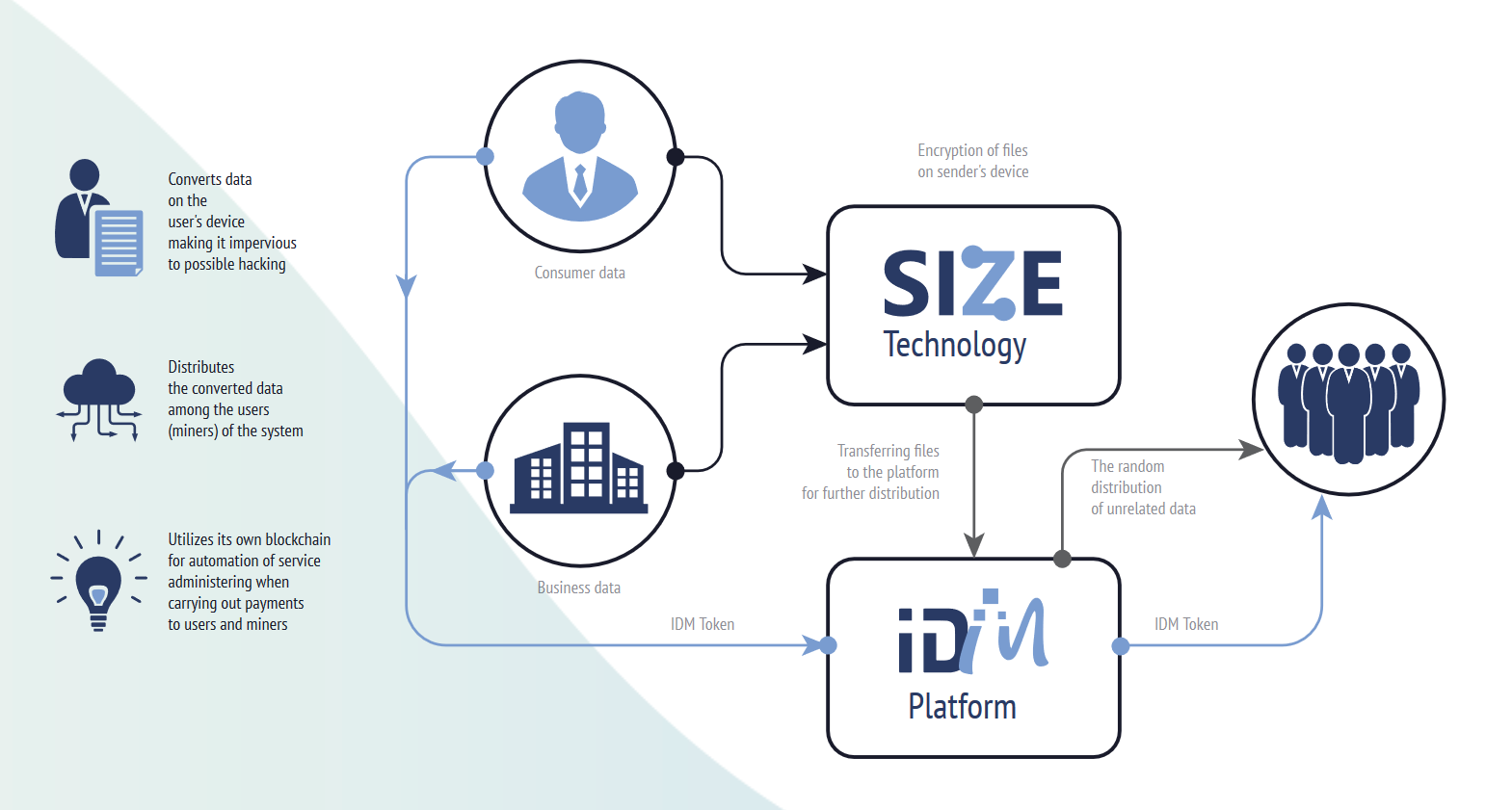
IDM can successfully compete with all cloud data storage services, as it offers following exclusive features:
o The most safe and secure data storage system and data transmission
o Affordable price
o The only player on the market offering this level of data protection
o Savvy marketing strategy
o Legal guarantee on data security
IDM focuses on strictly defined segments of the consumer and business market, and takes advantage of a competitive market opportunity, namely the demand for secure data storage.
Solution to the global problem
Global expansion of the IDM data storage service powered by SIZE technology, will prevent consumers and businesses from losing data, and therefore, from suffering losses associated with hacker attacks and theft of information
PROJECT OBJECTIVES
The main objective of this project is to raise funds for the development and scaling of the existing data storage service, combining SIZE, the innovative technology of post-quantum encryption, with the blockchain.
- Protect your information today and tomorrow
In the foreseeable future quantum computers will be able to break practically all existing types of cipher. For this reason, it is vitally important to start solving the problem of future data protection today. IDM service has solved this problem - Secure data storage is a vital necessity
The highest level of data protection, previously available only to government structures, is now available to public. IDM will become the new important attribute of everyone's life just like an ID card.
IDM is a public service with protection surpassing existing government standards for secure storage of information
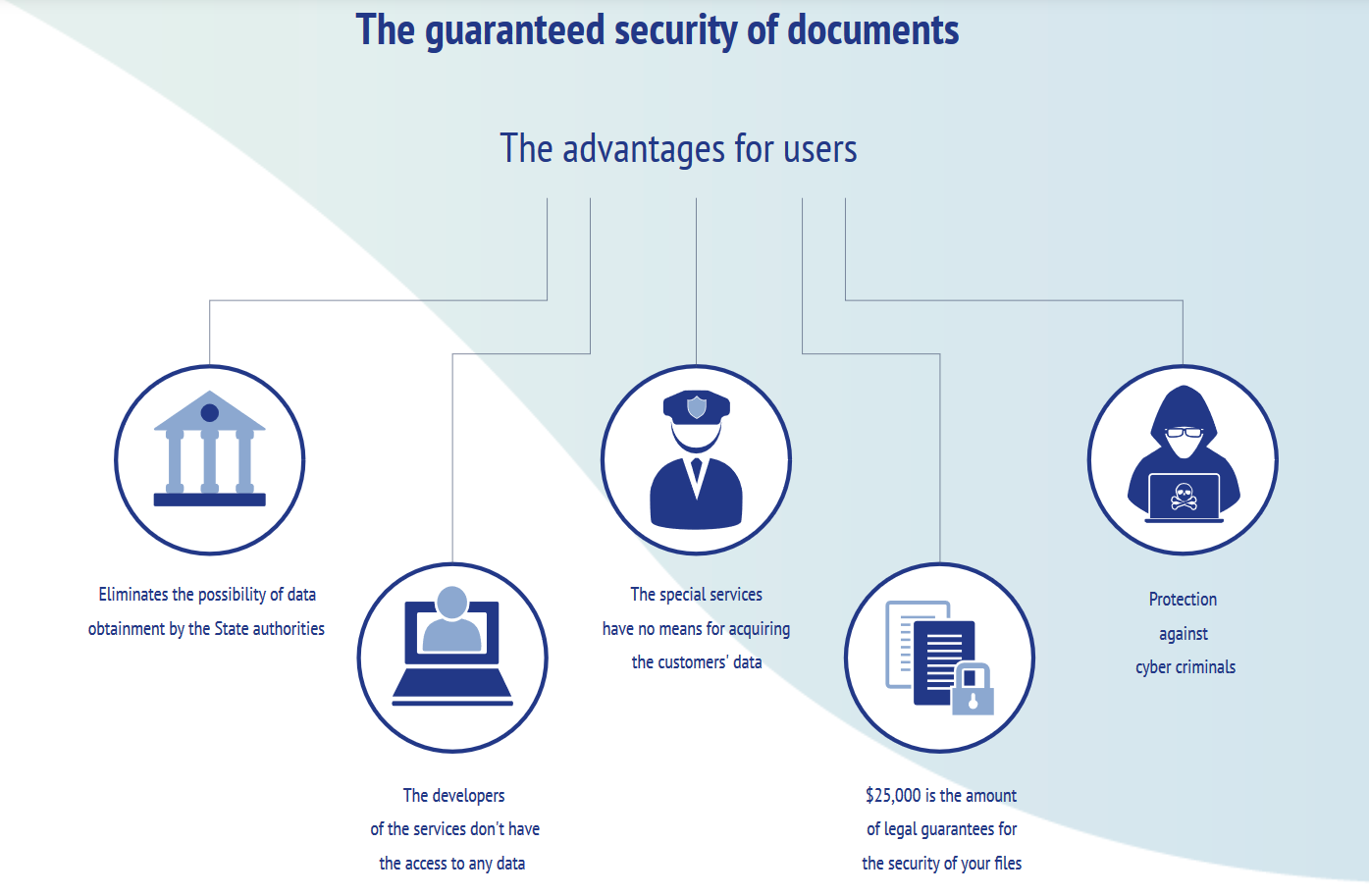
Currently, there isn't a single data storage on the market that can guarantee the absolute security of the documents that have special value and, at the same time, is accessible for the ordinary people.

OUR PATENTED TECHNOLOGY HAS THE FOLLOWING FEATURES:
o Highest level of data protection –the absolute cypher, the “one-time pad” principle and the post-quantum level of protection;
o No“backdoor” - the working principle of the system does not permit the creation of a functional backdoor;
o The system configuration doesnot permit a successful (MiTM) hacker attack;
o The service does not operate via DNS servers;
o No metadata collection - all metadata is generated and stored only on users' computers and is never transmitted over the Internet;
o Independent metadata management system allowing users to manage, protect and search within the stored information;
o Fully protected personal communication channel based on our own technology;
o Possibility for full recovery of a file even if the 98% of stored data has been lost;
o Automatic recovery and replication of the information from unreliable storage nodes, preventing reliability of the stored information falling to a critical level where recovery is impossible;
o Inherent scalability. The ecosystem is easily scalable, depending on the number of active storage nodes;
o Non-susceptibility to a risk of massive rolling disconnections of storage nodes in countries and on entire continents, which may happen due to natural disasters, power outages, enforcement of bans by governments or other competent authorities, due to the distribution of transformed data for the storage across all continents and throughout the world;
o Full autonomy of the ecosystem: the SIZE algorithm performs the monitoring of storage nodes, the quality of individual nodes, their reputation and distribution of data -whereas all settlements with users and miners are administered via blockchain;
o Ability to generate revenue from leasing unused memory on mobile or home devices;
o Second life of memory, the possibility of using obsolete and no longer used devices;
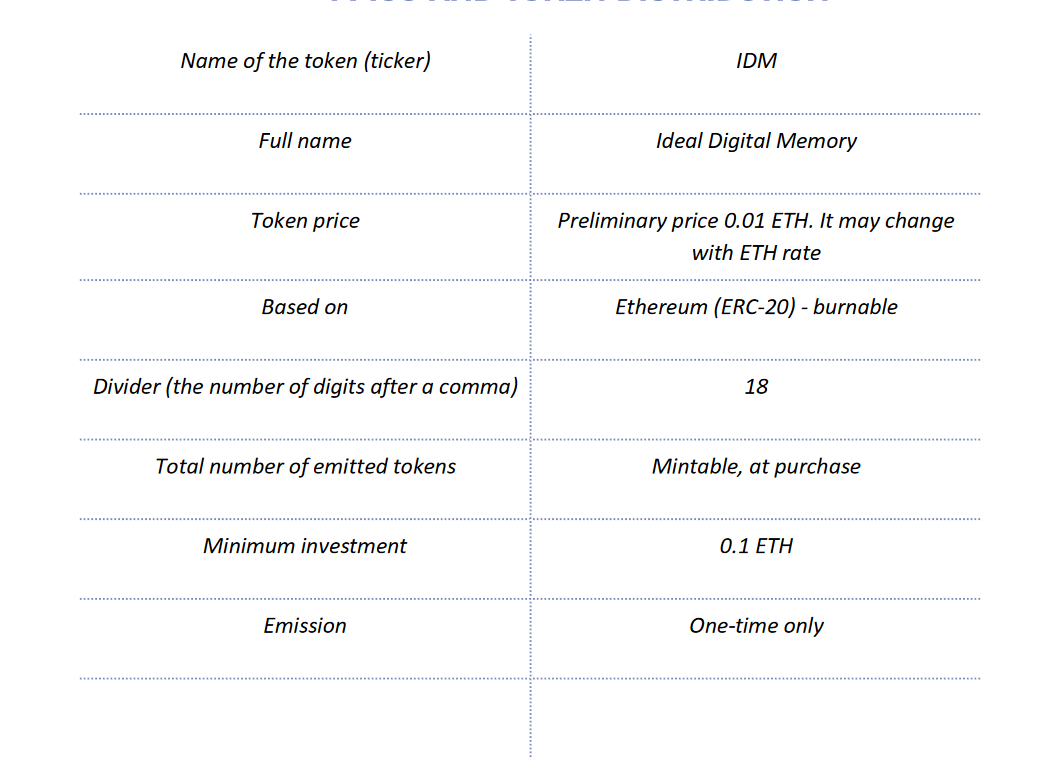
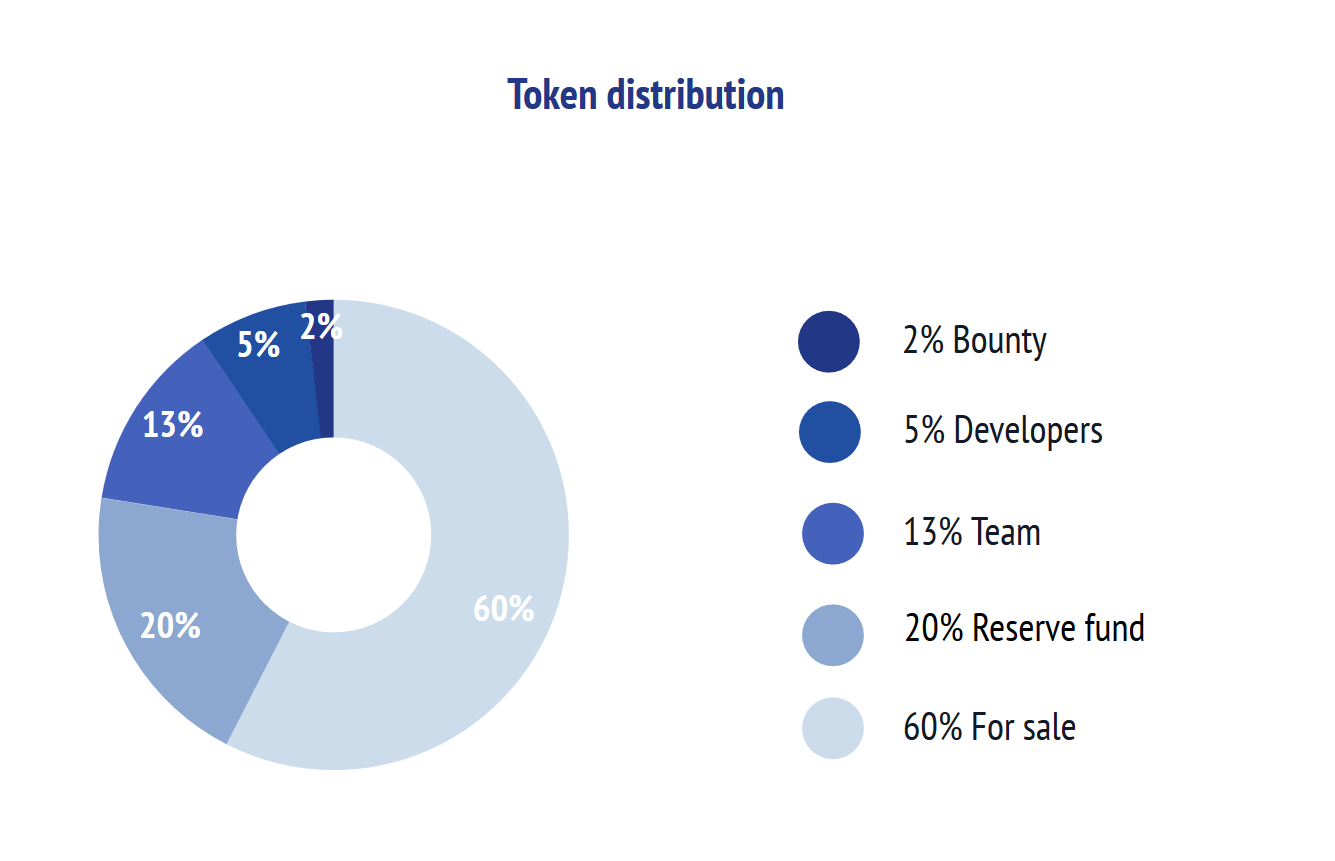
*ICO & TOKEN DISTRIBUTION
TOKEN DETAILS
KYC PROCEDURE
The IDM tokens cannot be transferred or sold to individuals or legal entities from the countries where the financial operations involving tokens are restricted or prohibited by law or will be restricted or prohibited after this document comes into force.
Our company does not permit participation of prohibited parties. We reserve the right to refuse or cancel the request for purchase of the IDM tokens at any time and at our own discretion if, in the course of the KYC procedure, we would have a reasonable suspicion that the potential buyer of the IDM tokens has provided a false, incomplete or misleading information or if the buyer is included in a group of people forbidden or otherwise restricted to purchase and use tokens.
ROADMAP
- 2010-The SIZE algorithm was successfully tested on CamGrid network at the Cavendish Laboratory at the University of Cambridge in the United Kingdom.
- 2012 –Foundation of Equivalence AG
- 2014-An ultra-secure file-sharingprogram based on SIZE technology was introduced at "Hack in Paris" where the global hacker community tried to crack the algorithm without success.
- 2015-The launch of a publicly available version of the BoobookBox for business and private users.
- March 2018-Technology has been successfully tested in European cybersecurity laboratories.
- April 2018-ICO for the global decentralized ultra-secure storage service IDM
- 2019 –Launch of IDM service
- 2019-Development of the cloud blockchain platform (SaaS) based on SIZE data protection technology
- 2019 -2020 -Implementation of a marketing strategy for the promotion of the IDM service and SIZE technology
- 2020 - 2022- Development of a decentralized and distributed cloud platform (PaaS)

For more information, please visit the links below:
Website : https://myidm.io/
Whitepaper : https://myidm.io/img/doc/wp_en.pdf
Ann Thread : https://bitcointalk.org/index.php?topic=3395543.msg35555064#msg35555064
Video : https://myidm.io/video/idm_720p_en.mp4
Facebook: https://www.facebook.com/IDMdatasec
Twitter: https://twitter.com/IDMdatasecurity
Reddit: https://www.reddit.com/user/IDMdatasecurity
Telegram : https://t.me/idmprotect_en
Author: Tosin David
My BitcoinTalk Profile: https://bitcointalk.org/index.php?action=profile;u=1180815
Disclaimer: This article was published in terms of the bounty campaign. I am not a project team member or its representative but a supporter of this incredible project.
Comments
Post a Comment